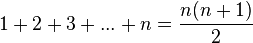Wednesday, September 30, 2009
Microsoft releases free computer security software
Microsoft Security Essentials is available for download at microsoft.com/security_essentials and is built on technology that the global software giant uses in computer security programs it designs for businesses.
"With Microsoft Security Essentials, consumers can get high-quality protection that is easy to get and easy to use, and it won't get in their way," said Amy Barzdukas, general manager for consumer security at Microsoft.
"Consumers have told us that they want the protection of real-time security software but we know that too many are either unwilling or unable to pay for it, and so end up unprotected."
Microsoft hopes that the free software will be broadly adopted, particularly by those who have not been vigilant about protecting computers from hackers, and thereby "increase security across the entire Windows ecosystem."
More than 90 percent of the computers worldwide run on Windows operating systems made by the US technology firm.
"Microsoft is helping to reduce some of the barriers that constrain consumers from running (anti-virus software)," said IDC security analyst Jon Crotty. "Microsoft is focused on the challenges that prevent consumers from running up-to-date anti-virus software today, particularly in emerging markets where there is a growing prevalence of malware."
Security Essentials is designed to run behind the scenes, defending machines against infection by malicious computer codes.
The real-time nature of the software means it is automatically kept up-to-date regarding viruses.
Computer security specialty firm Symantec downplayed the Microsoft offering, saying it is lightweight and isn't tuned for new forms of attack being used by hackers.
Symantec referred to Security Essentials as a stripped-down version of an old Microsoft OneCare product that got poor ratings.
"From a security perspective, this Microsoft tool offers reduced defenses at a critical point in the battle against cyber crime," Symantec said of the free offering that competes with Norton products sold by the firm.
"Unique malware and social engineering tricks fly under the radar of traditional signature-based technology alone -- which is what is employed by free security tools such as Microsoft's," it said.
Tuesday, September 29, 2009
Human-Computer Information Retrieval in Layman’s Terms
A few days ago, I was exchanging email with serial entrepreneur Chris Dixon about human-computer information retrieval (HCIR). He’d just looked through the accepted submissions list for HCIR 2009 and said, if I may paraphrase: this is great stuff, but it needs to be better communicated for broader consumption. I quickly shot back a reaction that I’ll excerpt here (when in doubt, make it public!):
At some level it’s blindingly obvious: to err is human, to really screw up takes a computer. The HealthBase fiasco isn’t a shocker: lots of people are skeptical of pure AI approaches.
What people don’t get is that you can work to optimize the division of labor. I’m evangelizing it in places like Technology Review–a bit more mainstream than my blog. But ultimately the message has to resonate with entrepreneurs and investors who will make that vision a reality. Endeca is all about HCIR. Bing is a step in the right direction for the open web. But there’s a long way to go.
His response: that’s a lot more consumable that any other description of HCIR he’d seen to date (and he’s a regular reader here!). Having just finished reading Steve Blank’s Four Steps to the Epiphany, I appreciate his point: in a new market, the most critical priority is educating the potential customers.
As a number of us prepare for the HCIR 2009 workshop, that’s something to keep in mind. There’s a natural tension between rigorous scholarship and mass communication, but some have the greatest scholars (e.g., Richard Feynman and Linus Pauling) have shown the way for us mere mortals. Indeed, in a field as cross-disciplinary as HCIR, we would do well to make our work and vision as broadly consumable as possible, albeit without oversimplifying it to the point that it is vapid or even misleading.
Generally speaking, I blog in order to convince people that some of the esoteric ideas I encounter–and the occasional ideas I am fortunate enough to conceive–are worthy of broader consideration. I started blogging in order to bring greater visibility to HCIR–to convince people that the choice between human and machine responsibility is a false dichtomy in almost every aspect of the information seeking process.
In grade school, I learned that division of labor is the cornerstone of civilization–perhaps and our adaptive process of allocating effort our greatest achievement as a species. As machines play an increasingly important role in our lives–and serve as the lenses through which seek and consume almost all information–it is key that we not forget our roots. Let us be neither Luddites nor passive participants, but rather let us help computers help us.
Monday, September 28, 2009
Computer recycler gives itself an upgrade
Not afraid of mice, are you?
Don't be embarrassed to admit it — many people are. Especially senior citizens who have never held a mouse and students who can't afford one.
That's why CREAM — Computer Reuse, Education and Marketing — is offering free computer education classes and a free Internet cafe in central Vancouver. It's there for folks who have never manipulated a computer mouse, traversed the globe via the Internet, or sent anybody an e-mail.
"We want to give free education away," said executive director Oso Martin. "We want you to have a computer, not an expensive paperweight."
On Saturday morning, CREAM unveiled its new digs at 5000 East Fourth Plain Boulevard, alongside Albertsons and the new Habitat for Humanity ReStore, CREAM's partner in keeping decent secondhand stuff out of landfills. ReStore does it with building materials; CREAM, which shares the ReStore's space, does it with computers.
Donated computers arrive at CREAM's workshop and thrift store in the ReStore space. They're tested by volunteers and students from Clark College's vocational training program. The truly hopeless are disassembled and prepared for recycling — CREAM gets 20 percent of its income by selling these recyclables on the market — but computers with a future are refurbished and either handed over to the Salvation Army, which distributes them for free to the needy, or sold for well-below-market prices at the CREAM thrift store. Those computers are loaded up with basic Microsoft software.
CREAM was born nearly a decade ago, according to Jim Mansfield of Clark County Public Works, as the federal government started considering the question of hazardous electronic waste — like mercury, cadmium and lead — in discarded computers. The city of Vancouver and Clark County started discussing ways to recycle electronic waste rather than throwing it away. The first collection brought in enough discarded electronics to fill two 50-foot trailer trucks. The next step, Mansfield said, was seeing how much of it could be returned to use.
"We started wondering, what if we brought together the recycling and re-use sides," he said.
CREAM was born as a county-driven program. And over the next six years, more than 230 computer units were refurbished and given to people who needed them. All told, 4 million pounds of electronic junk was diverted from the waste stream and recycled or returned to use.
Because of changes in state law, CREAM has now spun off as a private nonprofit — working with $330,000 in start-up funding from the city and county, Martin said. It's looking to raise about $50,000 more to keep remodeling its new space — adding an actual classroom, as well as more computers and stipends for instructors. Plus, a big sign.
Martin said there are 100 computers in the CREAM pipeline right now. That's many times CREAM's old rate of processing, he said.
"It's great to see this stuff going out to people who can't afford it," said John Walway, a Clark College student and computer help-desk worker. "If both sides of the fence aren't getting their hands on technology, some are going to get left way behind."
Right now, the education CREAM offers is basic Internet literacy for the mouse-fearing — how to do e-mail, how to move around the World Wide Web, how to post pictures or résumés online.
"Especially for senior citizens who are a little afraid of technology and they're just trying to get over that barrier," he said.
Rory Bowman said the local Macintosh users group, called Apple Van, will begin meeting at CREAM. His mother, Glenna, said she's ready to sign up as an instructor.
Vancouver Mayor Royce Pollard said the CREAM program is a winner on many levels. It provides computer training for students and job seekers, a free space for eager learners, and a shot in the arm for the Fourth Plain corridor — one of the city's biggest revitalization targets.
"Right now, not far from here, there are a whole lot of teenagers sleeping," he said. "They're going to find out that they've got access to the whole world right here. What better place to do it?"
Sunday, September 27, 2009
Hewlett-Packard - Intel dealings laid bare in European report
At the heart of the European antitrust case against Intel are a series of once-confidential memos that provide a rare glimpse into the intense and at times acrimonious negotiations between the world's biggest chip maker and Hewlett-Packard, the world's biggest computer company.
Even a company as powerful as HP, the documents suggest, had to make business decisions based on how Intel would react. The Palo Alto computer company reportedly was so worried about threats from Intel that it dramatically scaled back its plans earlier this decade to sell computers powered by chips from Intel competitor Advanced Micro Devices of Sunnyvale.
And when AMD offered HP 1 million free microprocessors, saying it was a gift "no reasonable business partner could refuse," HP took only 160,000 to avoid Intel retaliation, according to the report unveiled last week by the European Commission.
But the significance of the e-mails and other documents, which were generated by the two Silicon Valley titans after HP introduced a business computer using AMD chips seven years ago, remains in dispute. HP declined a Mercury News request to be interviewed and Intel insists it did nothing illegal, calling the commission's findings "wrong as a matter of fact, law, economics and elementary fairness."
Founded in 1968, Santa Clara-based Intel has long dominated the market for x86 microprocessors, the brains of most personal computers and servers. But AMD, formed a year
--------------------------------------------------------------------------------
Advertisement
--------------------------------------------------------------------------------
later, began making serious inroads into that business about 10 years ago as the quality of its chips improved. Then, on Aug. 19, 2002, HP introduced a business desktop computer in the United States with an AMD x86 chip, the first major computer maker to do so. That prompted Intel, HPs biggest chip supplier, to step up the pressure, the commission's report said.
At the time, HP had been negotiating to get a new round of Intel rebates, a form of financial incentive Intel has used for years to persuade computer companies to buy its chips. The deals tended to be renegotiated every few months, but how much Intel paid was not made public in the commission's report.
Although many rebates are perfectly legal, antitrust regulators contend large companies can misuse the payments to dominate their markets. In fining Intel a record $1.45 billion, the European Commission claimed the chip maker limited competition and, thus, consumer choice, by threatening to reduce or eliminate its rebates to customers who bought too many AMD chips. And it cited Intel's dealings with HP as a prime example.
AMD had gotten its chips into some consumer computers by 2002, and it hoped HP would help it expand into the lucrative business computer market. But a month before HP introduced the AMD-powered computer, according to the commission report, HP was already getting nervous about how Intel would react.
The commission cited an HP memo asking AMD to establish a multimillion-dollar fund, "which HP can draw from as compensation for potential 'retaliatory' acts from Intel." The memo added that HP feared losing Intel's rebates and even worried that Intel might punish HP by giving "unusual discounts" to an HP competitor.
When HP finally introduced the controversial business computer, "Intel reacted very negatively," according to an HP document cited by the commission, and for a time the chip maker broke off its rebate negotiations with HP. Eventually, HP and Intel resumed their talks. But the arrangement they worked out slammed AMD hard, making HP reluctant to reveal the terms to AMD.
"PLEASE DO NOT communicate to the regions, your team members or AMD" what HP has agreed to, an HP executive pleaded in an e-mail to Intel.
Besides requiring HP to buy 95 percent of the chips for its corporate desktop computers from Intel, the deal discouraged HP from selling the AMD-powered computers to big businesses or through HP's regular distributors, the commission said. It also delayed the computer's launch in Europe, the Middle East and Africa by six months.
A couple of years later, an HP executive asked in a memo if the company could sell the AMD-based computers through HP's regular distributors in parts of Europe and the Middle East, "and let Intel react if they discover it?" But another HP executive replied, "You can NOT," because of the chance that Intel would find out and halt its rebates to HP. "The risk is too high."
Since 2002, AMD has managed to increase its share of HP's chip business from about 13 percent to about 19 percent, with Intel controlling the rest, according to data gathered by research firm Gartner. But AMD today supplies only about 16 percent of the chips used in HP's business computers, which Chuck Diamond, AMD's lead lawyer in a pending antitrust lawsuit the company has filed against Intel, blames on the restrictive rebate deal HP worked out with Intel.
"That was devastating to AMD," Diamond said.
However, in an extensive response to the commission's report, Intel contends the European regulatory body — which the chip maker derided as having acted as investigator, prosecutor and judge — "reached indefensible conclusions."
According to Intel, which has appealed the commission's findings to Europe's Court of First Instance in Luxembourg, the evidence hardly suggests AMD has been damaged by Intel's rebates.
AMD not only has grabbed a bigger share of the microprocessor market over the past decade, Intel argues, but HP and the four other computer makers mentioned in the commission's report increased their combined purchases of AMD chips by 533 percent from 2002 to 2007, the main period of the report's focus.
Consumers also have benefitted over the same period, Intel claims, because the microprocessor market has seen "dramatically lower prices, significantly greater output of product and exponentially improved performance."
As for the allegation that Intel bullied computer makers, Intel counters that much of the commission's report is based on "documentary fragments" from low-level employees who didn't understand Intel's relationship with its customers.
In fact, Intel insists the computer companies played Intel and AMD off of each other to get the lowest chip prices and weren't intimidated at all by Intel. As evidence, Intel gave the Mercury News a summary of a deposition Dell gave in the ongoing suit filed by AMD, which asserted that "Intel never threatened Dell with retaliation if Dell bought microprocessors from AMD," even after Dell began using AMD's chips in 2006.
In HP's case, Intel contends the Palo Alto company came up with the idea of limiting AMD to 5 percent of HP's chip supplies and that HP chose to buy most of its microprocessors from Intel "because of the superiority of Intel's offer, taking into account customer demand for Intel and AMD."
Thursday, September 24, 2009
Determining the best email service: Gmail, Hotmail, or Yahoo
What's the best online email service? They're all wonderful in that they let you access your email from a Web browser, which means just about any computer anywhere. So what it comes down to for me, having had a Hotmail account, and still using Yahoo!, Gmail and even Netscape/AOL accounts, was how well each site worked, how fast they were, and what features they offered. And over the years, I've slowly migrated all of my email from Gmail and would not think of looking back. I keep the Yahoo! and Netscape/AOL account just because I've had them forever, so I check them once a month, but Gmail is running on at least two of my PCs at all times.
Why Gmail? For starters, it's fast and always available, and even on the rare times you get an error, you usually get a funny message that will give you chuckle while you hit the reload button and it goes away.
What's nice about Gmail is how powerful it is if you have Javascript enabled. It automatically adds anyone you send to or receive email from to your address book ("Contacts") which you can also add/remove entries by hand, and has a nice "Frequently Used Addresses" which gleans the hundreds or thousands of addresses you'll end up having saved down to the two dozen you use the most.
The other big win with Gmail is that its spam filters are by far the best, although it's nice enough to save all the spam in a folder in case you accidently get a message filtered that wasn't spam. I've been using Gmail since the original Beta launch and was one of the first 1000 users, and I've never had a message sent to the spam filter by accident. Reporting spam is easy too - just click a box next to the message or open it, click the "Report Spam" button and away it goes - and by everyone doing that, the system helps catch spam before you see it. I only report about one piece of spam per week, although 80% of the mail to my two accounts is spam. I don't even have to delete it - I can laugh as it piles up, and Gmail automagically deletes anything older than 30 days. Plenty of time to find something accidently filtered, but no need to actually delete anything by hand. Perfect!
The last killer feature is the labeling method. Google rethought the whole idea of putting messages in folders - after all, when I order something for my home business from an online site, should I put it in the "Online Orders" folder, the "Taxes" folder (in case I need to show a receipt for my tax write-offs), my "Work" folder, or my "Technical" folder, since it's for technical work? Confused? Well, Google's approach is nothing short of brilliant and revolutionary. Instead of putting a message in a folder and trying to remember which one, or worse, making four copies for four folders, you just add labels to each message, and then when you "Archive" a message, it's simply taken out of your inbox but is available if you look under any of the labels you added to it. It's allowed me to keep tons of email over the last four years organized and easy to find.
The search feature works great, is extremely fast, and you can search based on particular labels, but I've found the labeling approach so intuitive that I have used the search perhaps only once a year. Once you get used to it, you'll never want to go back. And the storage space is huge, it's 2.5GB, 100 times bigger than the other systems, and deleted/spam messages don't count against the amount you have.
The last feature I've only finally started to use and is not available on any of the other systems is the built-in IM chat. You can install a separate chat client program on your computer like you need for Yahoo! or AOL, and add Yet Another Program to the pile. But everyone now and then I'll find myself in rapid back-and-forth email discussion with someone, and being able to just go to their contact and open a Web window that allows me to chat with them is just like being able to pick up the phone and call them: you can take a discussion that is just too much work to do in email and make it real time with the built-in IM. I don't use it often, but when I do, I'm very happy it's there, and it really lets me get things done quickly.
Gmail is more than just an Online Email Client, it's a work system that you can use to organize not just your email, but information, time, etc. It's become a crucial tool both in my personal and business life, and I can't imagine going back to the old, out-dated systems like Hotmail and the rest. If someone asks me what "Web 2.0" means, I use Gmail as an example: a Web application that really improves your life and makes you productive, rather than a distraction or curiosity.
If you don't yet have a Gmail account, simply go to http://mail.google.com and click on the link to create a new account. It's free, they ask for very limited person information, and takes moments to set up. The system has a lot of help available if you need it, but it's so intuitive that even my Mom, who's an energetic grandmother, figured it out without asking me for help, ever. And for anything to do with computers, that alone should convince you just how easy to use Gmail is, with very powerful tools available if you need them but not forced on you and easily ignored if you don't need or want them.
It's easy, free, and maybe even fun. I recommend checking it out immediately if you have Webmail / Online Email accounts ASAP! Cheers, Wink
Basic principles of computer security
As an IT and Security instructor I frequently get asked the question "What should I be doing to protect and secure my computer?" In response to this question I give a lot of the usual answers plus a host of other suggestions that can and will make a system more secure and make one less of a target. When I decided to write this article I decided that I would put together a list of "Tips and tricks" to assist you, the reader, in making your system more secure.
The following list I put together as a checklist and is not meant to imply any step is necessarily more important than another.
Antivirus Program: Chances are a good number of you reading this article will have an antivirus scanner in place, however there are still more than a few computer users who do not. The reality is that everyone should have an antivirus program installed, running and most importantly up-to-date. There are currently a number of options to choose from including Norton and McAfee or free versions from vendors like Grisoft (www. grisoft.com), so if you do not have one, get one today.
Trivia: Recent surveys suggest that between 25% and 35% of computer users worldwide have virus protection installed.
Firewalls: Firewalls serve a very important function which is controlling the flow of traffic on and off a computer thereby stopping unauthorized ingress and egress of data. Firewalls become even a bigger issue for those of you who have a) broadband b) use wireless or c) use public hot-spots as such connections all expose one to higher risk than older, slower connection standards such a dial-up. Great options for firewalls include, on the software side, Kerio, Norton and Zonealarm or hardware solutions such as dialup.
Tip: Not sure how well your firewall is working? Want to test it out? Browse over to the "Shields Up" utility over at (www.grc.com) and put your firewall to the test.
Updates and Patches: Keeping your system up-to-date with the latest patches first and foremost ensures that you are not only staying current with your software it also ensures that you do not have any nasty "holes" to be exploited. An example of what happens when patches are overlooked think back to the Nimda worm from 2001, this same worm is still infecting some Microsoft web servers today simply because some system admins have not installed a patch from 5 years ago.
Complex Passwords: Passwords are one of your first lines of defense against an attack, but sadly they are overlooked quite often until it is too late.
Those that do use passwords tend to overlook basic safety with passwords by not using what is called password complexity; password complexity refers to a password that has the following characteristics:
oUpper and lower case letters
oSpecial characters such as @ % or $
oAre at least 7 or 8 characters long
oAre not words found in the dictionary or are easy to guess
Using these simple guidelines to construct a password makes it significantly harder to break and therefore a successful deterrent against an attacker.
Trivia: The most common place to find the password of a user who has written it down? On a Post it note under their keyboard (no kidding).
Backing up: Backing up represents one of the final options if your system finally decides that it is going to take an "Extended leave" when you need it most. You should ideally be backing up your computer on a regular basis either daily or weekly (depending on your own needs) to a medium such as tape, CD or DVD.
Do you really need that?: Most people have a lot of software installed on their machine, but the question is how much of that do they actually use? Uninstalling applications you do not ever use or just plain do not need, reduces what security professionals call your "Attack surface" or possible ways for someone to attack you. A great place to start is to look at those applications that came bundled with your PC when you bought it. If you do not need it, do not patch it just uninstall it.
Can we get some service here?: In Windows (XP Pro and Windows 2000 Only) you might have heard of something called Services, which run in the background on your machine. Services provide features such as file sharing, networking enhancements and many other system features both obvious and otherwise. The problem is that more services are started in Windows than are normally needed, but they are started anyway to make the system useable by the greatest number of people. Shutting down unnecessary services can not only make your system run faster, but can also reduce the number of ways some can attack you. Basically if it is not running, it cannot be exploited. Not sure what to shut off? Take a look at this helpful URL for guidance (http://www.liutilities.com/pr od-ucts/wintaskspro/processlib rary/)
Note: Shutting down services if done correctly can be a great way to make a system more secure and perform better. Shutting down the wrong service can make a system unable to boot, so exercise caution.
Using the preceding tips can make you much more secure than you would be otherwise. I usually recommend these as a first line of defense. If you are feeling brave you can take this even further. The important thing to remember when trying to secure a system, (whether it is a single PC or an entire network) is that it can never be 100% secure. However, you can make yourself less of a target by making it harder to go after your system.
Thursday, September 17, 2009
Computer
Computer
| This article may be too long to comfortably read and navigate. Please consider splitting content into sub-articles and using this article for a summary of the key points of the subject. (June 2009) |
A computer is a machine that manipulates data according to a set of instructions.
Although mechanical examples of computers have existed through much of recorded human history, the first electronic computers were developed in the mid-20th century (1940–1945). These were the size of a large room, consuming as much power as several hundred modern personal computers (PCs).[1] Modern computers based on integrated circuits are millions to billions of times more capable than the early machines, and occupy a fraction of the space.[2] Simple computers are small enough to fit into a wristwatch, and can be powered by a watch battery. Personal computers in their various forms are icons of the Information Age and are what most people think of as "computers". The embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are however the most numerous.
The ability to store and execute lists of instructions called programs makes computers extremely versatile, distinguishing them from calculators. The Church–Turing thesis is a mathematical statement of this versatility: any computer with a certain minimum capability is, in principle, capable of performing the same tasks that any other computer can perform. Therefore computers ranging from a mobile phone to a supercomputer are all able to perform the same computational tasks, given enough time and storage capacity.
Contents[hide] |
History of computing

The first use of the word "computer" was recorded in 1613, referring to a person who carried out calculations, or computations, and the word continued to be used in that sense until the middle of the 20th century. From the end of the 19th century onwards though, the word began to take on its more familiar meaning, describing a machine that carries out computations.[3]
The history of the modern computer begins with two separate technologies—automated calculation and programmability—but no single device can be identified as the earliest computer, partly because of the inconsistent application of that term. Examples of early mechanical calculating devices include the abacus, the slide rule and arguably the astrolabe and the Antikythera mechanism (which dates from about 150–100 BC). Hero of Alexandria (c. 10–70 AD) built a mechanical theater which performed a play lasting 10 minutes and was operated by a complex system of ropes and drums that might be considered to be a means of deciding which parts of the mechanism performed which actions and when.[4] This is the essence of programmability.
The "castle clock", an astronomical clock invented by Al-Jazari in 1206, is considered to be the earliest programmable analog computer.[5] It displayed the zodiac, the solar and lunar orbits, a crescent moon-shaped pointer travelling across a gateway causing automatic doors to open every hour,[6][7] and five robotic musicians who played music when struck by levers operated by a camshaft attached to a water wheel. The length of day and night could be re-programmed to compensate for the changing lengths of day and night throughout the year.[5]
The Renaissance saw a re-invigoration of European mathematics and engineering. Wilhelm Schickard's 1623 device was the first of a number of mechanical calculators constructed by European engineers, but none fit the modern definition of a computer, because they could not be programmed.
In 1801, Joseph Marie Jacquard made an improvement to the textile loom by introducing a series of punched paper cards as a template which allowed his loom to weave intricate patterns automatically. The resulting Jacquard loom was an important step in the development of computers because the use of punched cards to define woven patterns can be viewed as an early, albeit limited, form of programmability.
It was the fusion of automatic calculation with programmability that produced the first recognizable computers. In 1837, Charles Babbage was the first to conceptualize and design a fully programmable mechanical computer, his analytical engine.[8] Limited finances and Babbage's inability to resist tinkering with the design meant that the device was never completed.
In the late 1880s, Herman Hollerith invented the recording of data on a machine readable medium. Prior uses of machine readable media, above, had been for control, not data. "After some initial trials with paper tape, he settled on punched cards ..."[9] To process these punched cards he invented the tabulator, and the keypunch machines. These three inventions were the foundation of the modern information processing industry. Large-scale automated data processing of punched cards was performed for the 1890 United States Census by Hollerith's company, which later became the core of IBM. By the end of the 19th century a number of technologies that would later prove useful in the realization of practical computers had begun to appear: the punched card, Boolean algebra, the vacuum tube (thermionic valve) and the teleprinter.
During the first half of the 20th century, many scientific computing needs were met by increasingly sophisticated analog computers, which used a direct mechanical or electrical model of the problem as a basis for computation. However, these were not programmable and generally lacked the versatility and accuracy of modern digital computers.
Alan Turing is widely regarded to be the father of modern computer science. In 1936 Turing provided an influential formalisation of the concept of the algorithm and computation with the Turing machine. Of his role in the modern computer, Time Magazine in naming Turing one of the 100 most influential people of the 20th century, states: "The fact remains that everyone who taps at a keyboard, opening a spreadsheet or a word-processing program, is working on an incarnation of a Turing machine." [10]
George Stibitz is internationally recognized as a father of the modern digital computer. While working at Bell Labs in November 1937, Stibitz invented and built a relay-based calculator he dubbed the "Model K" (for "kitchen table", on which he had assembled it), which was the first to use binary circuits to perform an arithmetic operation. Later models added greater sophistication including complex arithmetic and programmability.[11]
| Name | First operational | Numeral system | Computing mechanism | Programming | Turing complete |
|---|---|---|---|---|---|
| Zuse Z3 (Germany) | May 1941 | Binary | Electro-mechanical | Program-controlled by punched film stock (but no conditional branch) | Yes (1998) |
| Atanasoff–Berry Computer (US) | 1942 | Binary | Electronic | Not programmable—single purpose | No |
| Colossus Mark 1 (UK) | February 1944 | Binary | Electronic | Program-controlled by patch cables and switches | No |
| Harvard Mark I – IBM ASCC (US) | May 1944 | Decimal | Electro-mechanical | Program-controlled by 24-channel punched paper tape (but no conditional branch) | No |
| Colossus Mark 2 (UK) | June 1944 | Binary | Electronic | Program-controlled by patch cables and switches | No |
| ENIAC (US) | July 1946 | Decimal | Electronic | Program-controlled by patch cables and switches | Yes |
| Manchester Small-Scale Experimental Machine (UK) | June 1948 | Binary | Electronic | Stored-program in Williams cathode ray tube memory | Yes |
| Modified ENIAC (US) | September 1948 | Decimal | Electronic | Program-controlled by patch cables and switches plus a primitive read-only stored programming mechanism using the Function Tables as program ROM | Yes |
| EDSAC (UK) | May 1949 | Binary | Electronic | Stored-program in mercury delay line memory | Yes |
| Manchester Mark 1 (UK) | October 1949 | Binary | Electronic | Stored-program in Williams cathode ray tube memory and magnetic drum memory | Yes |
| CSIRAC (Australia) | November 1949 | Binary | Electronic | Stored-program in mercury delay line memory | Yes |
A succession of steadily more powerful and flexible computing devices were constructed in the 1930s and 1940s, gradually adding the key features that are seen in modern computers. The use of digital electronics (largely invented by Claude Shannon in 1937) and more flexible programmability were vitally important steps, but defining one point along this road as "the first digital electronic computer" is difficult.Shannon 1940 Notable achievements include:
]]
- Konrad Zuse's electromechanical "Z machines". The Z3 (1941) was the first working machine featuring binary arithmetic, including floating point arithmetic and a measure of programmability. In 1998 the Z3 was proved to be Turing complete, therefore being the world's first operational computer.[citation needed]
- The non-programmable Atanasoff–Berry Computer (1941) which used vacuum tube based computation, binary numbers, and regenerative capacitor memory. The use of regenerative memory allowed it to be much more compact then its peers (being approximately the size of a large desk or workbench), since intermediate results could be stored and then fed back into the same set of computation elements.
- The secret British Colossus computers (1943),[12] which had limited programmability but demonstrated that a device using thousands of tubes could be reasonably reliable and electronically reprogrammable. It was used for breaking German wartime codes.
- The Harvard Mark I (1944), a large-scale electromechanical computer with limited programmability.
- The U.S. Army's Ballistic Research Laboratory ENIAC (1946), which used decimal arithmetic and is sometimes called the first general purpose electronic computer (since Konrad Zuse's Z3 of 1941 used electromagnets instead of electronics). Initially, however, ENIAC had an inflexible architecture which essentially required rewiring to change its programming.
Several developers of ENIAC, recognizing its flaws, came up with a far more flexible and elegant design, which came to be known as the "stored program architecture" or von Neumann architecture. This design was first formally described by John von Neumann in the paper First Draft of a Report on the EDVAC, distributed in 1945. A number of projects to develop computers based on the stored-program architecture commenced around this time, the first of these being completed in Great Britain. The first to be demonstrated working was the Manchester Small-Scale Experimental Machine (SSEM or "Baby"), while the EDSAC, completed a year after SSEM, was the first practical implementation of the stored program design. Shortly thereafter, the machine originally described by von Neumann's paper—EDVAC—was completed but did not see full-time use for an additional two years.
Nearly all modern computers implement some form of the stored-program architecture, making it the single trait by which the word "computer" is now defined. While the technologies used in computers have changed dramatically since the first electronic, general-purpose computers of the 1940s, most still use the von Neumann architecture.
Computers using vacuum tubes as their electronic elements were in use throughout the 1950s, but by the 1960s had been largely replaced by transistor-based machines, which were smaller, faster, cheaper to produce, required less power, and were more reliable. The first transistorised computer was demonstrated at the University of Manchester in 1953.[13] In the 1970s, integrated circuit technology and the subsequent creation of microprocessors, such as the Intel 4004, further decreased size and cost and further increased speed and reliability of computers. By the late 1970s, many products such as video recorders contained dedicated computers called microcontrollers, and they started to appear as a replacement to mechanical controls in domestic appliances such as washing machines. The 1980s witnessed home computers and the now ubiquitous personal computer. With the evolution of the Internet, personal computers are becoming as common as the television and the telephone in the household.
Modern smartphones are fully-programmable computers in their own right, and as of 2009 may well be the most common form of such computers in existence.
Stored program architecture
The defining feature of modern computers which distinguishes them from all other machines is that they can be programmed. That is to say that a list of instructions (the program) can be given to the computer and it will store them and carry them out at some time in the future.
In most cases, computer instructions are simple: add one number to another, move some data from one location to another, send a message to some external device, etc. These instructions are read from the computer's memory and are generally carried out (executed) in the order they were given. However, there are usually specialized instructions to tell the computer to jump ahead or backwards to some other place in the program and to carry on executing from there. These are called "jump" instructions (or branches). Furthermore, jump instructions may be made to happen conditionally so that different sequences of instructions may be used depending on the result of some previous calculation or some external event. Many computers directly support subroutines by providing a type of jump that "remembers" the location it jumped from and another instruction to return to the instruction following that jump instruction.
Program execution might be likened to reading a book. While a person will normally read each word and line in sequence, they may at times jump back to an earlier place in the text or skip sections that are not of interest. Similarly, a computer may sometimes go back and repeat the instructions in some section of the program over and over again until some internal condition is met. This is called the flow of control within the program and it is what allows the computer to perform tasks repeatedly without human intervention.
Comparatively, a person using a pocket calculator can perform a basic arithmetic operation such as adding two numbers with just a few button presses. But to add together all of the numbers from 1 to 1,000 would take thousands of button presses and a lot of time—with a near certainty of making a mistake. On the other hand, a computer may be programmed to do this with just a few simple instructions. For example:
mov #0,sum ; set sum to 0
mov #1,num ; set num to 1
loop: add num,sum ; add num to sum
add #1,num ; add 1 to num
cmp num,#1000 ; compare num to 1000
ble loop ; if num <= 1000, go back to 'loop' halt ; end of program. stop running
Once told to run this program, the computer will perform the repetitive addition task without further human intervention. It will almost never make a mistake and a modern PC can complete the task in about a millionth of a second.[14]
However, computers cannot "think" for themselves in the sense that they only solve problems in exactly the way they are programmed to. An intelligent human faced with the above addition task might soon realize that instead of actually adding up all the numbers one can simply use the equation
and arrive at the correct answer (500,500) with little work.[15] In other words, a computer programmed to add up the numbers one by one as in the example above would do exactly that without regard to efficiency or alternative solutions.
Programs

In practical terms, a computer program may run from just a few instructions to many millions of instructions, as in a program for a word processor or a web browser. A typical modern computer can execute billions of instructions per second (gigahertz or GHz) and rarely make a mistake over many years of operation. Large computer programs consisting of several million instructions may take teams of programmers years to write, and due to the complexity of the task almost certainly contain errors.
Errors in computer programs are called "bugs". Bugs may be benign and not affect the usefulness of the program, or have only subtle effects. But in some cases they may cause the program to "hang"—become unresponsive to input such as mouse clicks or keystrokes, or to completely fail or "crash". Otherwise benign bugs may sometimes may be harnessed for malicious intent by an unscrupulous user writing an "exploit"—code designed to take advantage of a bug and disrupt a program's proper execution. Bugs are usually not the fault of the computer. Since computers merely execute the instructions they are given, bugs are nearly always the result of programmer error or an oversight made in the program's design.[16]
In most computers, individual instructions are stored as machine code with each instruction being given a unique number (its operation code or opcode for short). The command to add two numbers together would have one opcode, the command to multiply them would have a different opcode and so on. The simplest computers are able to perform any of a handful of different instructions; the more complex computers have several hundred to choose from—each with a unique numerical code. Since the computer's memory is able to store numbers, it can also store the instruction codes. This leads to the important fact that entire programs (which are just lists of instructions) can be represented as lists of numbers and can themselves be manipulated inside the computer just as if they were numeric data. The fundamental concept of storing programs in the computer's memory alongside the data they operate on is the crux of the von Neumann, or stored program, architecture. In some cases, a computer might store some or all of its program in memory that is kept separate from the data it operates on. This is called the Harvard architecture after the Harvard Mark I computer. Modern von Neumann computers display some traits of the Harvard architecture in their designs, such as in CPU caches.
While it is possible to write computer programs as long lists of numbers (machine language) and this technique was used with many early computers,[17] it is extremely tedious to do so in practice, especially for complicated programs. Instead, each basic instruction can be given a short name that is indicative of its function and easy to remember—a mnemonic such as ADD, SUB, MULT or JUMP. These mnemonics are collectively known as a computer's assembly language. Converting programs written in assembly language into something the computer can actually understand (machine language) is usually done by a computer program called an assembler. Machine languages and the assembly languages that represent them (collectively termed low-level programming languages) tend to be unique to a particular type of computer. For instance, an ARM architecture computer (such as may be found in a PDA or a hand-held videogame) cannot understand the machine language of an Intel Pentium or the AMD Athlon 64 computer that might be in a PC.[18]
Though considerably easier than in machine language, writing long programs in assembly language is often difficult and error prone. Therefore, most complicated programs are written in more abstract high-level programming languages that are able to express the needs of the programmer more conveniently (and thereby help reduce programmer error). High level languages are usually "compiled" into machine language (or sometimes into assembly language and then into machine language) using another computer program called a compiler.[19] Since high level languages are more abstract than assembly language, it is possible to use different compilers to translate the same high level language program into the machine language of many different types of computer. This is part of the means by which software like video games may be made available for different computer architectures such as personal computers and various video game consoles.
The task of developing large software systems presents a significant intellectual challenge. Producing software with an acceptably high reliability within a predictable schedule and budget has historically been difficult; the academic and professional discipline of software engineering concentrates specifically on this challenge.
Example
Suppose a computer is being employed to drive a traffic light at an intersection between two streets. The computer has the following three basic instructions.
- ON(Streetname, Color) Turns the light on Streetname with a specified Color on.
- OFF(Streetname, Color) Turns the light on Streetname with a specified Color off.
- WAIT(Seconds) Waits a specifed number of seconds.
- START Starts the program
- REPEAT Tells the computer to repeat a specified part of the program in a loop.
Comments are marked with a // on the left margin. Comments in a computer program do not affect the operation of the program. They are not evaluated by the computer. Assume the streetnames are Broadway and Main.
START
//Let Broadway traffic go
OFF(Broadway, Red)
ON(Broadway, Green)
WAIT(60 seconds)
//Stop Broadway traffic
OFF(Broadway, Green)
ON(Broadway, Yellow)
WAIT(3 seconds)
OFF(Broadway, Yellow)
ON(Broadway, Red)
//Let Main traffic go
OFF(Main, Red)
ON(Main, Green)
WAIT(60 seconds)
//Stop Main traffic
OFF(Main, Green)
ON(Main, Yellow)
WAIT(3 seconds)
OFF(Main, Yellow)
ON(Main, Red)
//Tell computer to continuously repeat the program.
REPEAT ALL
With this set of instructions, the computer would cycle the light continually through red, green, yellow and back to red again on both streets.
However, suppose there is a simple on/off switch connected to the computer that is intended to be used to make the light flash red while some maintenance operation is being performed. The program might then instruct the computer to:
START
IF Switch == OFF then: //Normal traffic signal operation
{
//Let Broadway traffic go
OFF(Broadway, Red)
ON(Broadway, Green)
WAIT(60 seconds)
//Stop Broadway traffic
OFF(Broadway, Green)
ON(Broadway, Yellow)
WAIT(3 seconds)
OFF(Broadway, Yellow)
ON(Broadway, Red)
//Let Main traffic go
OFF(Main, Red)
ON(Main, Green)
WAIT(60 seconds)
//Stop Main traffic
OFF(Main, Green)
ON(Main, Yellow)
WAIT(3 seconds)
OFF(Main, Yellow)
ON(Main, Red)
//Tell the computer to repeat this section continuously.
REPEAT THIS SECTION
}
IF Switch == ON THEN: //Maintenance Mode
{
//Turn the red lights on and wait 1 second.
ON(Broadway, Red)
ON(Main, Red)
WAIT(1 second)
//Turn the red lights off and wait 1 second.
OFF(Broadway, Red)
OFF(Main, Red)
WAIT(1 second)
//Tell the comptuer to repeat the statements in this section.
REPEAT THIS SECTION
}
In this manner, the traffic signal will run a flash-red program when the switch is on, and will run the normal program when the switch is off. Both of these program examples show the basic layout of a computer program in a simple, familiar context of a traffic signal. Any experienced programmer can spot many software bugs in the program, for instance, not making sure that the green light is off when the switch is set to flash red. However, to remove all possible bugs would make this program much longer and more complicated, and would be confusing to nontechnical readers: the aim of this example is a simple demonstration of how computer instructions are laid out.
Function
A general purpose computer has four main components: the arithmetic logic unit (ALU), the control unit, the memory, and the input and output devices (collectively termed I/O). These parts are interconnected by busses, often made of groups of wires.
Inside each of these parts are thousands to trillions of small electrical circuits which can be turned off or on by means of an electronic switch. Each circuit represents a bit (binary digit) of information so that when the circuit is on it represents a "1", and when off it represents a "0" (in positive logic representation). The circuits are arranged in logic gates so that one or more of the circuits may control the state of one or more of the other circuits.
The control unit, ALU, registers, and basic I/O (and often other hardware closely linked with these) are collectively known as a central processing unit (CPU). Early CPUs were composed of many separate components but since the mid-1970s CPUs have typically been constructed on a single integrated circuit called a microprocessor.
Control unit
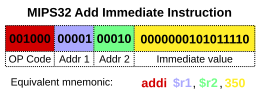
The control unit (often called a control system or central controller) manages the computer's various components; it reads and interprets (decodes) the program instructions, transforming them into a series of control signals which activate other parts of the computer.[20] Control systems in advanced computers may change the order of some instructions so as to improve performance.
A key component common to all CPUs is the program counter, a special memory cell (a register) that keeps track of which location in memory the next instruction is to be read from.[21]
The control system's function is as follows—note that this is a simplified description, and some of these steps may be performed concurrently or in a different order depending on the type of CPU:
- Read the code for the next instruction from the cell indicated by the program counter.
- Decode the numerical code for the instruction into a set of commands or signals for each of the other systems.
- Increment the program counter so it points to the next instruction.
- Read whatever data the instruction requires from cells in memory (or perhaps from an input device). The location of this required data is typically stored within the instruction code.
- Provide the necessary data to an ALU or register.
- If the instruction requires an ALU or specialized hardware to complete, instruct the hardware to perform the requested operation.
- Write the result from the ALU back to a memory location or to a register or perhaps an output device.
- Jump back to step (1).
Since the program counter is (conceptually) just another set of memory cells, it can be changed by calculations done in the ALU. Adding 100 to the program counter would cause the next instruction to be read from a place 100 locations further down the program. Instructions that modify the program counter are often known as "jumps" and allow for loops (instructions that are repeated by the computer) and often conditional instruction execution (both examples of control flow).
It is noticeable that the sequence of operations that the control unit goes through to process an instruction is in itself like a short computer program—and indeed, in some more complex CPU designs, there is another yet smaller computer called a microsequencer that runs a microcode program that causes all of these events to happen.
Arithmetic/logic unit (ALU)
The ALU is capable of performing two classes of operations: arithmetic and logic.[22]
The set of arithmetic operations that a particular ALU supports may be limited to adding and subtracting or might include multiplying or dividing, trigonometry functions (sine, cosine, etc) and square roots. Some can only operate on whole numbers (integers) whilst others use floating point to represent real numbers—albeit with limited precision. However, any computer that is capable of performing just the simplest operations can be programmed to break down the more complex operations into simple steps that it can perform. Therefore, any computer can be programmed to perform any arithmetic operation—although it will take more time to do so if its ALU does not directly support the operation. An ALU may also compare numbers and return boolean truth values (true or false) depending on whether one is equal to, greater than or less than the other ("is 64 greater than 65?").
Logic operations involve Boolean logic: AND, OR, XOR and NOT. These can be useful both for creating complicated conditional statements and processing boolean logic.
Superscalar computers may contain multiple ALUs so that they can process several instructions at the same time.[23] Graphics processors and computers with SIMD and MIMD features often provide ALUs that can perform arithmetic on vectors and matrices.
Memory

A computer's memory can be viewed as a list of cells into which numbers can be placed or read. Each cell has a numbered "address" and can store a single number. The computer can be instructed to "put the number 123 into the cell numbered 1357" or to "add the number that is in cell 1357 to the number that is in cell 2468 and put the answer into cell 1595". The information stored in memory may represent practically anything. Letters, numbers, even computer instructions can be placed into memory with equal ease. Since the CPU does not differentiate between different types of information, it is the software's responsibility to give significance to what the memory sees as nothing but a series of numbers.
In almost all modern computers, each memory cell is set up to store binary numbers in groups of eight bits (called a byte). Each byte is able to represent 256 different numbers (2^8 = 256); either from 0 to 255 or -128 to +127. To store larger numbers, several consecutive bytes may be used (typically, two, four or eight). When negative numbers are required, they are usually stored in two's complement notation. Other arrangements are possible, but are usually not seen outside of specialized applications or historical contexts. A computer can store any kind of information in memory if it can be represented numerically. Modern computers have billions or even trillions of bytes of memory.
The CPU contains a special set of memory cells called registers that can be read and written to much more rapidly than the main memory area. There are typically between two and one hundred registers depending on the type of CPU. Registers are used for the most frequently needed data items to avoid having to access main memory every time data is needed. As data is constantly being worked on, reducing the need to access main memory (which is often slow compared to the ALU and control units) greatly increases the computer's speed.
Computer main memory comes in two principal varieties: random-access memory or RAM and read-only memory or ROM. RAM can be read and written to anytime the CPU commands it, but ROM is pre-loaded with data and software that never changes, so the CPU can only read from it. ROM is typically used to store the computer's initial start-up instructions. In general, the contents of RAM are erased when the power to the computer is turned off, but ROM retains its data indefinitely. In a PC, the ROM contains a specialized program called the BIOS that orchestrates loading the computer's operating system from the hard disk drive into RAM whenever the computer is turned on or reset. In embedded computers, which frequently do not have disk drives, all of the required software may be stored in ROM. Software stored in ROM is often called firmware, because it is notionally more like hardware than software. Flash memory blurs the distinction between ROM and RAM, as it retains its data when turned off but is also rewritable. It is typically much slower than conventional ROM and RAM however, so its use is restricted to applications where high speed is unnecessary.[24]
In more sophisticated computers there may be one or more RAM cache memories which are slower than registers but faster than main memory. Generally computers with this sort of cache are designed to move frequently needed data into the cache automatically, often without the need for any intervention on the programmer's part.
Input/output (I/O)

I/O is the means by which a computer exchanges information with the outside world.[25] Devices that provide input or output to the computer are called peripherals.[26] On a typical personal computer, peripherals include input devices like the keyboard and mouse, and output devices such as the display and printer. Hard disk drives, floppy disk drives and optical disc drives serve as both input and output devices. Computer networking is another form of I/O.
Often, I/O devices are complex computers in their own right with their own CPU and memory. A graphics processing unit might contain fifty or more tiny computers that perform the calculations necessary to display 3D graphics[citation needed]. Modern desktop computers contain many smaller computers that assist the main CPU in performing I/O.
Multitasking
While a computer may be viewed as running one gigantic program stored in its main memory, in some systems it is necessary to give the appearance of running several programs simultaneously. This is achieved by multitasking i.e. having the computer switch rapidly between running each program in turn.[27]
One means by which this is done is with a special signal called an interrupt which can periodically cause the computer to stop executing instructions where it was and do something else instead. By remembering where it was executing prior to the interrupt, the computer can return to that task later. If several programs are running "at the same time", then the interrupt generator might be causing several hundred interrupts per second, causing a program switch each time. Since modern computers typically execute instructions several orders of magnitude faster than human perception, it may appear that many programs are running at the same time even though only one is ever executing in any given instant. This method of multitasking is sometimes termed "time-sharing" since each program is allocated a "slice" of time in turn.[28]
Before the era of cheap computers, the principle use for multitasking was to allow many people to share the same computer.
Seemingly, multitasking would cause a computer that is switching between several programs to run more slowly — in direct proportion to the number of programs it is running. However, most programs spend much of their time waiting for slow input/output devices to complete their tasks. If a program is waiting for the user to click on the mouse or press a key on the keyboard, then it will not take a "time slice" until the event it is waiting for has occurred. This frees up time for other programs to execute so that many programs may be run at the same time without unacceptable speed loss.
Multiprocessing

Some computers are designed to distribute their work across several CPUs in a multiprocessing configuration, a technique once employed only in large and powerful machines such as supercomputers, mainframe computers and servers. Multiprocessor and multi-core (multiple CPUs on a single integrated circuit) personal and laptop computers are now widely available, and are being increasingly used in lower-end markets as a result.
Supercomputers in particular often have highly unique architectures that differ significantly from the basic stored-program architecture and from general purpose computers.[29] They often feature thousands of CPUs, customized high-speed interconnects, and specialized computing hardware. Such designs tend to be useful only for specialized tasks due to the large scale of program organization required to successfully utilize most of the available resources at once. Supercomputers usually see usage in large-scale simulation, graphics rendering, and cryptography applications, as well as with other so-called "embarrassingly parallel" tasks.
Networking and the Internet
Computers have been used to coordinate information between multiple locations since the 1950s. The U.S. military's SAGE system was the first large-scale example of such a system, which led to a number of special-purpose commercial systems like Sabre.[30]
In the 1970s, computer engineers at research institutions throughout the United States began to link their computers together using telecommunications technology. This effort was funded by ARPA (now DARPA), and the computer network that it produced was called the ARPANET.[31] The technologies that made the Arpanet possible spread and evolved.
In time, the network spread beyond academic and military institutions and became known as the Internet. The emergence of networking involved a redefinition of the nature and boundaries of the computer. Computer operating systems and applications were modified to include the ability to define and access the resources of other computers on the network, such as peripheral devices, stored information, and the like, as extensions of the resources of an individual computer. Initially these facilities were available primarily to people working in high-tech environments, but in the 1990s the spread of applications like e-mail and the World Wide Web, combined with the development of cheap, fast networking technologies like Ethernet and ADSL saw computer networking become almost ubiquitous. In fact, the number of computers that are networked is growing phenomenally. A very large proportion of personal computers regularly connect to the Internet to communicate and receive information. "Wireless" networking, often utilizing mobile phone networks, has meant networking is becoming increasingly ubiquitous even in mobile computing environments.
Further topics
Hardware
The term hardware covers all of those parts of a computer that are tangible objects. Circuits, displays, power supplies, cables, keyboards, printers and mice are all hardware.
| Peripheral device (Input/output) | Input | Mouse, Keyboard, Joystick, Image scanner, Webcam, Graphics tablet, Microphone |
| Output | Monitor, Printer, Loudspeaker | |
| Both | Floppy disk drive, Hard disk drive, Optical disc drive, Teleprinter | |
| Computer busses | Short range | RS-232, SCSI, PCI, USB |
| Long range (Computer networking) | Ethernet, ATM, FDDI |
Software
Software refers to parts of the computer which do not have a material form, such as programs, data, protocols, etc. When software is stored in hardware that cannot easily be modified (such as BIOS ROM in an IBM PC compatible), it is sometimes called "firmware" to indicate that it falls into an uncertain area somewhere between hardware and software.
Programming languages
Programming languages provide various ways of specifying programs for computers to run. Unlike natural languages, programming languages are designed to permit no ambiguity and to be concise. They are purely written languages and are often difficult to read aloud. They are generally either translated into machine code by a compiler or an assembler before being run, or translated directly at run time by an interpreter. Sometimes programs are executed by a hybrid method of the two techniques. There are thousands of different programming languages—some intended to be general purpose, others useful only for highly specialized applications.
| Lists of programming languages | Timeline of programming languages, List of programming languages by category, Generational list of programming languages, List of programming languages, Non-English-based programming languages |
| Commonly used Assembly languages | ARM, MIPS, x86 |
| Commonly used high-level programming languages | Ada, BASIC, C, C++, C#, COBOL, Fortran, Java, Lisp, Pascal, Object Pascal |
| Commonly used Scripting languages | Bourne script, JavaScript, Python, Ruby, PHP, Perl |
Professions and organizations
As the use of computers has spread throughout society, there are an increasing number of careers involving computers.
The need for computers to work well together and to be able to exchange information has spawned the need for many standards organizations, clubs and societies of both a formal and informal nature.
| Standards groups | ANSI, IEC, IEEE, IETF, ISO, W3C |
| Professional Societies | ACM, ACM Special Interest Groups, IET, IFIP, BCS |
| Free/Open source software groups | Free Software Foundation, Mozilla Foundation, Apache Software Foundation |
See also
- Computability theory (computer science)
- Computer generated holography
- Computer security and Computer insecurity
- Electronic waste
- List of computer term etymologies
- List of fictional computers
- Living computers theory
- Pulse computer
- The Secret Guide to Computers (book)
- Platform virtualization
Notes
- ^ In 1946, ENIAC required an estimated 174 kW. By comparison, a modern laptop computer may use around 30 W; nearly six thousand times less. "Approximate Desktop & Notebook Power Usage". University of Pennsylvania. http://www.upenn.edu/computing/provider/docs/hardware/powerusage.html. Retrieved 2009-06-20.
- ^ Early computers such as Colossus and ENIAC were able to process between 5 and 100 operations per second. A modern "commodity" microprocessor (as of 2007) can process billions of operations per second, and many of these operations are more complicated and useful than early computer operations. "Intel® Core™2 Duo Mobile Processor: Features". Intel Corporation. http://www.intel.com/cd/channel/reseller/asmo-na/eng/products/mobile/processors/core2duo_m/feature/index.htm. Retrieved 2009-06-20.
- ^ computer, n., Oxford English Dictionary (2 ed.), Oxford University Press, 1989, http://dictionary.oed.com/, retrieved 2009-04-10
- ^ "Heron of Alexandria". http://www.mlahanas.de/Greeks/HeronAlexandria2.htm. Retrieved 2008-01-15.
- ^ a b Ancient Discoveries, Episode 11: Ancient Robots, History Channel, http://www.youtube.com/watch?v=rxjbaQl0ad8, retrieved 2008-09-06
- ^ Howard R. Turner (1997), Science in Medieval Islam: An Illustrated Introduction, p. 184, University of Texas Press, ISBN 0-292-78149-0
- ^ Donald Routledge Hill, "Mechanical Engineering in the Medieval Near East", Scientific American, May 1991, pp. 64-9 (cf. Donald Routledge Hill, Mechanical Engineering)
- ^ The analytical engine should not be confused with Babbage's difference engine which was a non-programmable mechanical calculator.
- ^ Columbia University Computing History: Herman Hollerith
- ^ "Alan Turing - Time 100 People of the Century". Time. http://www.time.com/time/time100/scientist/profile/turing.html. Retrieved 2009-06-13. "The fact remains that everyone who taps at a keyboard, opening a spreadsheet or a word-processing program, is working on an incarnation of a Turing machine"
- ^ "Inventor Profile: George R. Stibitz". National Inventors Hall of Fame Foundation, Inc.. http://www.invent.org/hall_of_fame/140.html.
- ^ B. Jack Copeland, ed., Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford University Press, 2006
- ^ Lavington 1998, p. 37
- ^ This program was written similarly to those for the PDP-11 minicomputer and shows some typical things a computer can do. All the text after the semicolons are comments for the benefit of human readers. These have no significance to the computer and are ignored. (Digital Equipment Corporation 1972)
- ^ Attempts are often made to create programs that can overcome this fundamental limitation of computers. Software that mimics learning and adaptation is part of artificial intelligence.
- ^ It is not universally true that bugs are solely due to programmer oversight. Computer hardware may fail or may itself have a fundamental problem that produces unexpected results in certain situations. For instance, the Pentium FDIV bug caused some Intel microprocessors in the early 1990s to produce inaccurate results for certain floating point division operations. This was caused by a flaw in the microprocessor design and resulted in a partial recall of the affected devices.
- ^ Even some later computers were commonly programmed directly in machine code. Some minicomputers like the DEC PDP-8 could be programmed directly from a panel of switches. However, this method was usually used only as part of the booting process. Most modern computers boot entirely automatically by reading a boot program from some non-volatile memory.
- ^ However, there is sometimes some form of machine language compatibility between different computers. An x86-64 compatible microprocessor like the AMD Athlon 64 is able to run most of the same programs that an Intel Core 2 microprocessor can, as well as programs designed for earlier microprocessors like the Intel Pentiums and Intel 80486. This contrasts with very early commercial computers, which were often one-of-a-kind and totally incompatible with other computers.
- ^ High level languages are also often interpreted rather than compiled. Interpreted languages are translated into machine code on the fly by another program called an interpreter.
- ^ The control unit's role in interpreting instructions has varied somewhat in the past. Although the control unit is solely responsible for instruction interpretation in most modern computers, this is not always the case. Many computers include some instructions that may only be partially interpreted by the control system and partially interpreted by another device. This is especially the case with specialized computing hardware that may be partially self-contained. For example, EDVAC, one of the earliest stored-program computers, used a central control unit that only interpreted four instructions. All of the arithmetic-related instructions were passed on to its arithmetic unit and further decoded there.
- ^ Instructions often occupy more than one memory address, so the program counters usually increases by the number of memory locations required to store one instruction.
- ^ David J. Eck (2000). The Most Complex Machine: A Survey of Computers and Computing. A K Peters, Ltd.. p. 54. ISBN 9781568811284.
- ^ Erricos John Kontoghiorghes (2006). Handbook of Parallel Computing and Statistics. CRC Press. p. 45. ISBN 9780824740672.
- ^ Flash memory also may only be rewritten a limited number of times before wearing out, making it less useful for heavy random access usage. (Verma 1988)
- ^ Donald Eadie (1968). Introduction to the Basic Computer. Prentice-Hall. p. 12.
- ^ Arpad Barna; Dan I. Porat (1976). Introduction to Microcomputers and the Microprocessors. Wiley. p. 85. ISBN 9780471050513.
- ^ Jerry Peek; Grace Todino, John Strang (2002). Learning the UNIX Operating System: A Concise Guide for the New User. O'Reilly. p. 130. ISBN 9780596002619.
- ^ Gillian M. Davis (2002). Noise Reduction in Speech Applications. CRC Press. p. 111. ISBN 9780849309496.
- ^ However, it is also very common to construct supercomputers out of many pieces of cheap commodity hardware; usually individual computers connected by networks. These so-called computer clusters can often provide supercomputer performance at a much lower cost than customized designs. While custom architectures are still used for most of the most powerful supercomputers, there has been a proliferation of cluster computers in recent years. (TOP500 2006)
- ^ Agatha C. Hughes (2000). Systems, Experts, and Computers. MIT Press. p. 161. ISBN 9780262082853. "The experience of SAGE helped make possible the first truly large-scale commercial real-time network: the SABRE computerized airline reservations system..."
- ^ "A Brief History of the Internet". Internet Society. http://www.isoc.org/internet/history/brief.shtml. Retrieved 2008-09-20.
- ^ Most major 64-bit instruction set architectures are extensions of earlier designs. All of the architectures listed in this table, except for Alpha, existed in 32-bit forms before their 64-bit incarnations were introduced.
References
- a Kempf, Karl (1961). Historical Monograph: Electronic Computers Within the Ordnance Corps. Aberdeen Proving Ground (United States Army). http://ed-thelen.org/comp-hist/U-S-Ord-61.html.
- a Phillips, Tony (2000). "The Antikythera Mechanism I". American Mathematical Society. http://www.math.sunysb.edu/~tony/whatsnew/column/antikytheraI-0400/kyth1.html. Retrieved 2006-04-05.
- a Shannon, Claude Elwood (1940). A symbolic analysis of relay and switching circuits. Massachusetts Institute of Technology. http://hdl.handle.net/1721.1/11173.
- a Digital Equipment Corporation (1972) (PDF). PDP-11/40 Processor Handbook. Maynard, MA: Digital Equipment Corporation. http://bitsavers.vt100.net/dec/www.computer.museum.uq.edu.au_mirror/D-09-30_PDP11-40_Processor_Handbook.pdf.
- a Verma, G.; Mielke, N. (1988). Reliability performance of ETOX based flash memories. IEEE International Reliability Physics Symposium.
- a Meuer, Hans; Strohmaier, Erich; Simon, Horst; Dongarra, Jack (2006-11-13). "Architectures Share Over Time". TOP500. http://www.top500.org/lists/2006/11/overtime/Architectures. Retrieved 2006-11-27.
- Lavington, Simon (1998), A History of Manchester Computers (2 ed.), Swindon: The British Computer Society, ISBN 0902505018
- Stokes, Jon (2007). Inside the Machine: An Illustrated Introduction to Microprocessors and Computer Architecture. San Francisco: No Starch Press. ISBN 978-1-59327-104-6.